All Posts

The start of a new year is synonymous with improved lifestyle patterns. If healthier eating habits have become your goal, you are in good company. And if you are finding yourself getting off-track by now, you are also in good company. Choosing consistency over perfection - and with SAS Food

What we do matters. For 50 years, SAS has helped customers turn data into decisions that move the world forward. In 2025, that impact came to life in more than 30 new customer stories – organizations using SAS to move faster, adapt with confidence and deliver outcomes that improve lives,
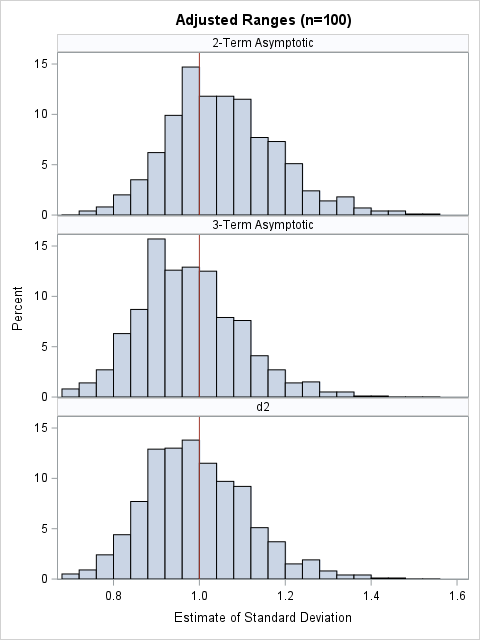
A previous article shows how to compute various robust estimates of scale in SAS. In that article, I show how to scale these robust estimators so that they become consistent estimators of the standard deviation (σ) when the data are normally distributed. The scaling factor is related to the expected

Regulatory pressure is real. Regulations keep piling up – ESG, GDPR, supply chain due diligence and now the EU AI Act. There’s no sign of it slowing down. And it’s not just regulators watching; customers, partners, and investors have rising expectations. The situation feels like a pressure cooker. Leaders in

Saber qual modelo de inteligência artificial usar para cada situação e como proteger dados de clientes é essencial quando organizações utilizam agentes de IA no atendimento ao cliente. Na segunda parte do artigo sobre esta tecnologia, conheça os pontos de atenção. No primeiro artigo desta série sobre agentes de inteligência

As despesas associadas a ecossistemas de agentes de IA podem aumentar rapidamente, assim como os problemas associados à falta de uma governança robusta. Entenda o que está em jogo no primeiro artigo da série sobre estes sistemas no contexto de atendimento ao cliente. Agentes de inteligência artificial (IA) vieram
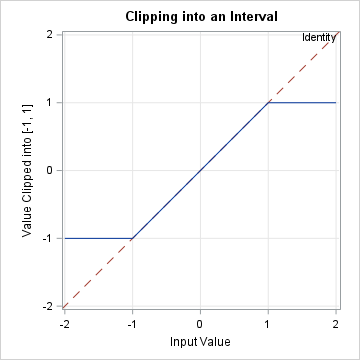
Years ago, I wrote an article about the "trap and cap" programming technique. The idea is that programmers should "trap" inputs to functions (like SQRT, LOG, and QUANTILE functions) to avoid domain errors. In addition, when visualizing a function's range, you should "cap" the output to improve graphs of functions

Organizações vivem um momento de transformação na forma como abordam a nova era prevenção à fraude, principalmente em relação aos dados que são usados para este fim. Para além dos dados transacionais tradicionais, uma tendência observada neste ano é o crescimento do uso de informações vindas de fontes como telemetria veicular, monitoramento

A revolução de dados que impulsiona a inteligência artificial nos coloca diante de um dilema jurídico, relacionado à inovação e privacidade no contexto jurídico: como equilibrar a necessidade de grandes quantidades de dados para a inovação com o direito fundamental à privacidade? Este desafio não é apenas técnico, mas também
Think of your data platform like an international airport. If every airline used different jetways. Each gate enforced its own security rules. And baggage systems couldn’t talk to each other. Nothing would scale. Planes would idle. Costs would spike. Delays would be constant. That’s effectively how many enterprise data estates
Last year was a big one for AI – especially regarding agents, large language models (LLMs) and digital twins. With every new advancement that changed our lives for the better came something equally complicating (trust and governance, for example), but I firmly believe AI is steering us in the right

We took a trip around campus, visiting some familiar locations with some old photos. 2026 marks 50 years of SAS. Undoubtedly, our software has changed the world, but there’s something else that’s been revolutionary: our workplace culture. A key part of that in Cary, NC, is our headquarters. To celebrate

Learn how to use SAS code (PROC HTTP) to read and write files from your Microsoft OneDrive, Microsoft Teams or SharePoint Online. You'll learn how to create a Microsoft Office 365 app, connect to it with SAS, and automate the integration with your office productivity environment.

Manufacturers operate some of the most complex machinery on the planet – from CNC machines and industrial robots to gas turbines with over 20,000 components. Keeping these assets running smoothly is mission-critical, yet maintenance teams are often buried under vague alerts, scattered documentation and time-consuming root cause analysis. Much of
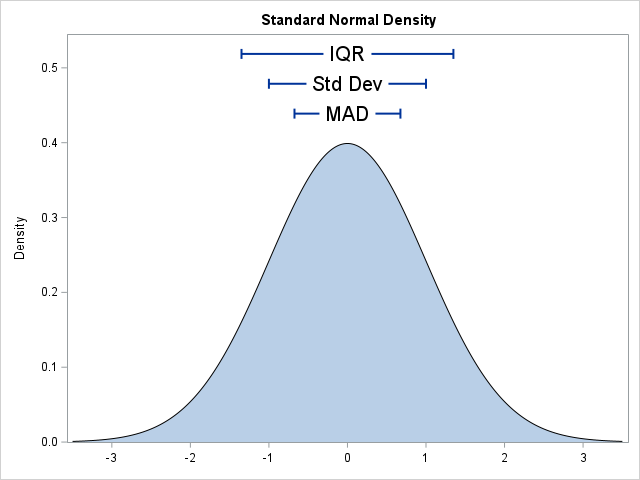
In statistics, the normal (Gaussian) distribution serves as a reference for many statistical quantities. For example, a normal distribution has excess kurtosis equal to zero, and other distributions are classified as leptokurtic (heavier-than-normal tails) or platykurtic (lighter-than-normal tails) in comparison. Similarly, the standard deviation of a normal distribution (σ) is











