SAS Users
Providing technical tips and support information, written for and by SAS users.
In the first of three posts on using automated analysis with SAS Visual Analytics, we explored a typical visualization designed to give telco customer care workers guidance on customers most receptive to upgrade their plans. While the analysis provided some insight, it lacked analytical depth -- and that increases the risk of wasting time, energy and

You're the operations director for a major telco's contact center. Your customer-care workers enjoy solving problems. Turning irate callers into fans makes their day. They also hate flying blind. They've been begging you for deeper insight into customer data to better serve their callers. They want to know which customers
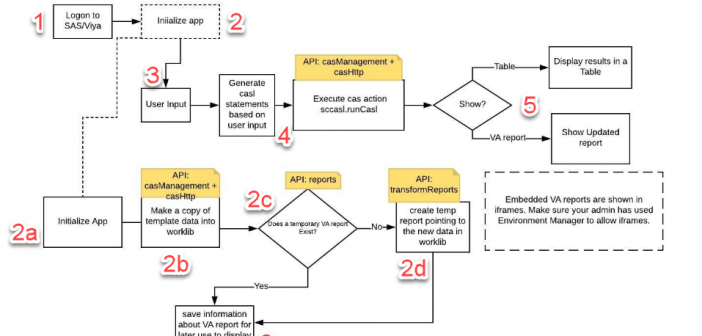
This post rounds out the year and my series of articles on SAS REST APIs. You can read all of my posts on this topic here. The first two articles in the series: Using SAS Viya REST APIs to access images from SAS Visual Analytics and Using SAS Cloud Analytics

