
2020 roundup: SAS Users YouTube channel how to tutorials
Find out the most popular SAS Users YouTube channel how to tutorials, and learn a thing or two!

Find out the most popular SAS Users YouTube channel how to tutorials, and learn a thing or two!
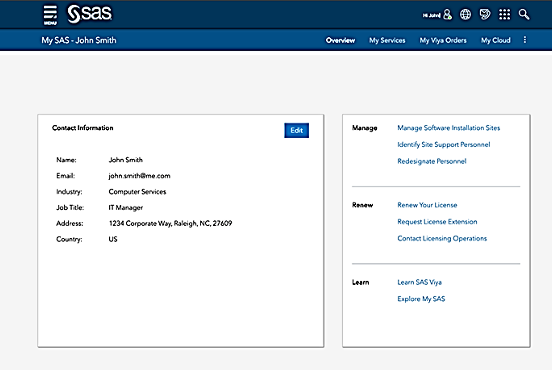
My SAS is a brand-new customer experience page. This new location takes a variety of customer service places and puts them in one interface. The goal of My SAS is to ensure all SAS customers have the best possible experience available in the marketplace.

If you’re like me and the rest of the conference team, you’ve probably attended more virtual events this year than you ever thought possible. You can see the general evolution of virtual events by watching the early ones from April or May and compare them to the recent ones. We