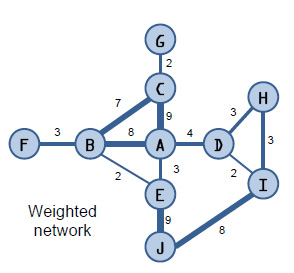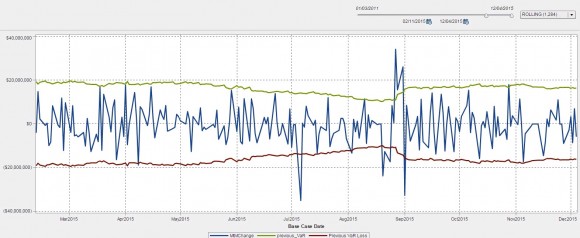
Year-end outlooks from most analysts project the low-price environment in the oil market will continue for most of next year, but some pundits emphasize that the market has bottomed out and suggest recovery, though gradual, may be seen if increasing demand outpaces supply growth and sops up some of the