Europol, the law enforcement agency of the European Union, in its recently released 2014 Internet Organized Crime Threat Assessment (iOCTA), cited a report by U.S. security firm IID that predicts that the first “online murder” will occur by year end, based on the number of computer security system flaws discovered by hackers.
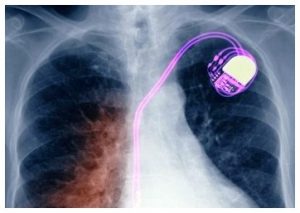 While there have been no reported cases of hacking-related deaths so far, former vice president Dick Cheney has had the wireless function on his implanted defibrillator disabled in order to prevent potential hackers from remotely accessing his device. Just such a scenario was played out fictionally in the political TV thriller Homeland, in which his counterpart was murdered by terrorists who were able to hack into the (fictional) vice president’s pacemaker. In an interview last year, Cheney said, “I was aware of the danger that existed and found it credible – [the scene in Homeland]was an accurate portrayal of what was possible.”
While there have been no reported cases of hacking-related deaths so far, former vice president Dick Cheney has had the wireless function on his implanted defibrillator disabled in order to prevent potential hackers from remotely accessing his device. Just such a scenario was played out fictionally in the political TV thriller Homeland, in which his counterpart was murdered by terrorists who were able to hack into the (fictional) vice president’s pacemaker. In an interview last year, Cheney said, “I was aware of the danger that existed and found it credible – [the scene in Homeland]was an accurate portrayal of what was possible.”
Cheney’s fears are not unfounded in the least. 2012 research from security vendor IOActive regarding the security shortcomings in the 4.5+ million pacemakers sold between 2006 and 2011 in the U.S turned up the following:
- Until recently, pacemakers were reprogrammed by medical staff using a wand that had to pass within a couple of meters of a patient, which flips a software switch that allows it to accept new instructions.
- But the trend is to go wireless. Several medical manufacturers are now selling bedside transmitters that replace the wand, with a range of up to 30 to 50 feet. With such a range, remote attacks become more feasible. For example, devices have been found to cough up their serial number and model number with a special command, making it is possible to reprogram the firmware of a pacemaker in a person's body. Other problems with the devices include the fact they often contain personal data about patients, such as their name and their doctor. The devices also have "backdoors," or ways that programmers can get access to them without the standard authentication - backdoors available for more nefarious uses.
- Just as your laptop scans the local environment searching for available WiFi networks, there is software out there that allows a user to scan for medical devices within range. A list will appear, and a user can select a device, such as a pacemaker, which can then be shut off or configured to deliver a shock if direct access can be obtained.
- As if this wasn't bad enough, it is possible to upload specially-crafted firmware to a company's servers that would infect multiple pacemakers, spreading through their systems like a real virus - we are potentially looking at a worm with the ability to commit mass murder.
Can it get worse? By now you’ve heard of SaaS (software-as-a-service) and PaaS (platform-as-a-service), but how about CaaS – Crime-as-a-Service? From the Europol report: “A service-based criminal industry is developing, in which specialists in the virtual underground economy develop products and services for use by other criminals. This 'Crime-as-a-Service' business model drives innovation and sophistication, and provides access to a wide range of services that facilitate almost any type of cybercrime. As a consequence, entry barriers into cybercrime are being lowered, allowing those lacking technical expertise - including traditional organized crime groups - to venture into cybercrime by purchasing the skills and tools they lack.”
Just take a moment to let that sink in: Lowering barriers to entry, criminal innovation, CaaS as a business model. It really shouldn’t surprise us, though - criminal enterprises have been adapting the principles of sound business management from the early days of organized crime. Did you know that the illegal drug market is a $2.5-trillion dollar industry? Not merely a billion dollar industry, it’s a TRILLION dollar industry, employing standard business school tactics such as quality control, freemium pricing models, upselling, risk management and branding, not to mention the ever changing supply chain and logistics challenges.
Cyber criminals are at least, if not more, sophisticated than the typical drug trade.
Lest you think that cyber security is primarily the province of the big banks and retailers, how your products will integrate with the Internet of Things (IoT) should make you think twice.
I went over twenty years with the same credit card number - now I have to get a new one pretty much every year because someone got hacked, and I’m guessing that your experience hasn’t been much different. And remember, these breaches are occurring at large enterprises already employing a significantly sized staff of cybersecurity experts.
If your device is going to be on the internet, security will need to be baked into the design from the very beginning. Again, from the Europol report: “"The Internet of Things represents a whole new attack vector that we believe criminals will already be looking for ways to exploit. The IoT is inevitable. We must expect a rapidly growing number of devices to be rendered 'smart' and thence to become interconnected. Unfortunately, we feel that it is equally inevitable that many of these devices will leave vulnerabilities via which access to networks can be gained by criminals.”
Rod Rasmussen, the president of IID - the source of the murder prediction mentioned at the beginning of this post - had this to say: "There's already this huge quasi-underground market where you can buy and sell vulnerabilities that have been discovered. Although the first ever reported internet murder is yet to happen, ‘death by internet’ is already a reality as seen from a number of suicides linked to personally-targeted online attacks.”
While it’s unlikely that anyone will die from a stolen credit card number, that’s not going to be the case for many of the tens of billions of devices attached to the internet, from medical devices to wearables to the connected car. As a manufacturer of current and potential IoT devices, you may not be aware of SAS’ dominant presence in the fraud detection/prevention and cybersecurity field. When you get a call from your bank freezing your credit card and questioning that $3,500 purchase at a shopping mall in Altoona, it was likely SAS analytics behind the scenes that identified and flagged the fraud.
If CaaS is going to be part of the criminal elements’ business model, cybersecurity will need to be part of your product design and IoT business model, and SAS can help. While your brand may survive a variety of production quality problems, it won't survive a murder on the IoT.
[You can also learn more about cybersecurity from Ray Boisvert, CEO and founder of I-Sec Integrated Strategies, at his presentation, “The Threat Landscape: Cyber Tools and Methods Transforming the Business Environment,” at SAS' Premier Business Leadership Series, Wednesday, Oct. 22, from 2:15 to 3 p.m. Boisvert sees cybersecurity as a task for analytics that can help organizations tease out the proverbial signal from the massive internet “noise” around serious threats. The challenge is to identify the right threat vector related to the most valued elements an organization holds dear. The organization will only be successful if it has technology to quickly digest huge streams of data, in real time, so that it may begin to see patterns that can thwart further attacks.]

4 Comments
Pingback: CaaS – Crime-as-a-Service: Murder on the Internet of Things | EPM Channel
Pingback: CyberCrime – What monsters are hiding under your bed? - Value Alley
Pingback: EPM Channel | CyberCrime: What Monsters Are Hiding Under Your Bed??
Pingback: Transparency and the Information arms race - Value Alley