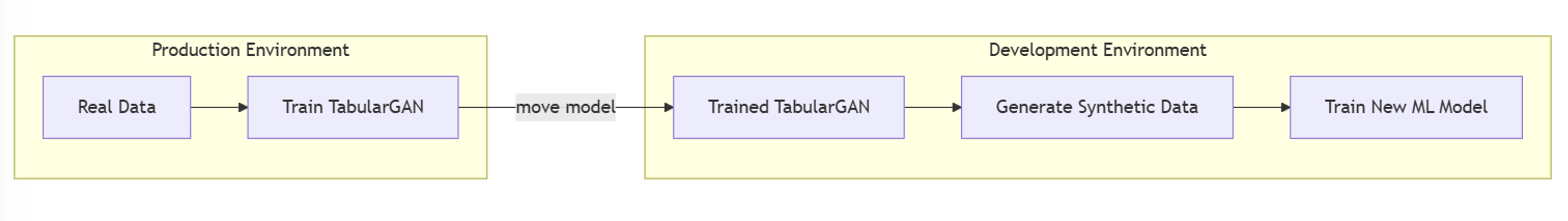
This article was co-written with Sundaresh Sankaran. The Artificial Intelligence (AI) era is here. To prevent harm, ensure proper governance and secure data, we need to trust our AI output. We must demonstrate that it operates in a fair and responsible manner with a high level of efficiency. As builders of