
Most of us have volunteered in some capacity -- as a guinea pig in a magic show, as a helping hand with a charity, or perhaps as a coach for a child’s sports team. Why do we do it? I think the cliché holds true. We get as much, or

Most of us have volunteered in some capacity -- as a guinea pig in a magic show, as a helping hand with a charity, or perhaps as a coach for a child’s sports team. Why do we do it? I think the cliché holds true. We get as much, or
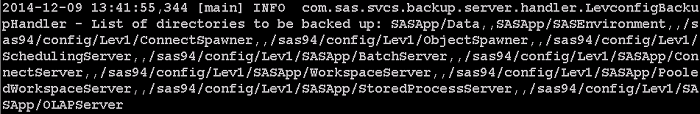
In researching material for an upcoming project, I investigated the SAS Deployment Backup and Recovery Tool available in SAS 9.4. Here are some of my findings on identifying what directories are included in a Backup and Recovery session and how to add custom directories to a backup configuration. The SAS

Life is a gift, and it offers us the privilege, opportunity, and responsibility to give something back by becoming more. - Anthony Robbins Every year at SAS Global Forum, SAS professionals from all over the globe gather, reconnect and learn from each other. And wherever they gather, SAS Global Forum

If you haven’t tried them for your web applications and other graphics needs, you’ll want to read further! Scalable Vector Graphics (SVG) output is vector graphics output you can display with most (if not all) modern web browsers. Because SVG graphic output is scalable, you can zoom in on the
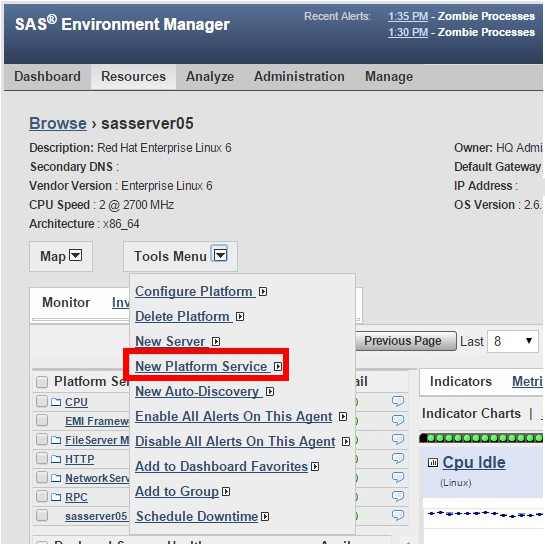
As SAS administrators, I know you are as excited as I am by the ability of SAS Environment Manager to monitor, in detail, the performance of their SAS environments. Now, we have a robust tool to monitor, measure and report on the performance of the various SAS components. An added

The application deadline for the SAS Global Forum 2015 Junior Professional Award has been extended to February 1! If you have fewer than three years’ experience using SAS in a professional setting, you’ll want to take a closer look at the requirements and apply online. Junior Professional Program Coordinators Sally
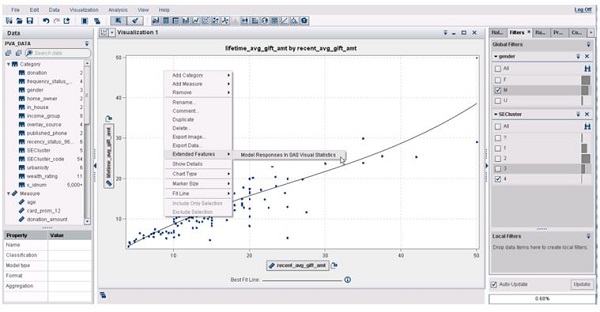
In case you haven’t read about SAS Visual Statistics, let’s start with a quick overview. First, it’s an add-on to SAS Visual Analytics. Second, it’s a web-based solution with an interactive, drag-and-drop interface that helps you rapidly build descriptive and predictive models. Lastly, SAS Visual Analytics and SAS Visual Statistics

In trying to offer better support to SAS users, many customers’ IT departments are looking to consolidate all their SAS desktop users onto a centralized Windows, UNIX or Linux server. This option is a very practical strategy, but implementing it satisfactorily requires a lot of assessment on how the SAS

Congratulations if you’re one of the over 300 presenters whose proposals for content were accepted for SAS Global Forum 2015! Now that it’s time to start preparing papers, posters and presentations, I thought this would be a good opportunity to write about the Presenter Mentoring Program, an excellent service offered
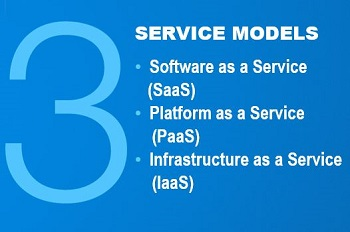
In a recent post, I talked about the 5 essential characteristics of cloud computing. In today’s post, I will cover the three service models available in the cloud as they are defined by the National Institute of Standards and Technology, or NIST. Like the story of Goldilocks, when it comes