ln SAS Viya, deployments identities are managed by the environments configured identity provider. In Visual SAS Viya deployments the identity provider must be an LDAP (Lightweight Directory Access Protocol) server. Initial setup of a SAS Viya Deployment requires configuration to support reading the identity information (users and groups) from LDAP. SAS Viya 3.3 adds support for multi-tenancy which has implications for the way users and groups must be stored in LDAP. For the SAS Administrator, this means at least a rudimentary understanding of LDAP is required. In this blog post, I will review some key LDAP basics for the SAS Viya administrator.
A basic understanding of LDAP ensures SAS Viya administrators can speak the same language as the LDAP administrator.
What is LDAP?
LDAP is a lightweight protocol for accessing directory servers. A directory server is a hierarchical object orientated database. An LDAP server can be used to organize anything. One of the most common uses is as an identity management system, to organize user and group membership.
LDAP directories are organized in a tree manner:
- A directory is a tree of directory entries.
- An entry contains a set of attributes.
- An attribute has a name, and one or more values.
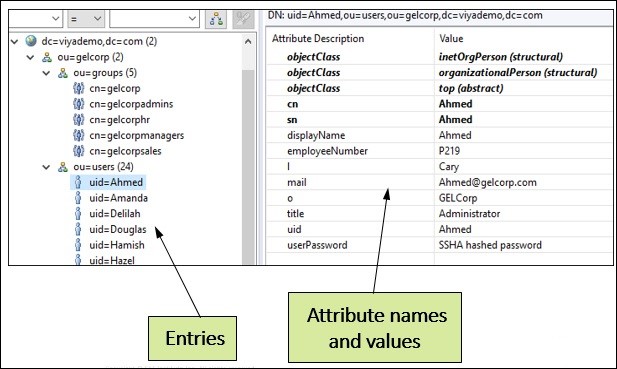
Below is an entry for a user Henrik. It has common attributes like:
- uid User id
- cn Common Name
- L Location
- DisplayName: name to display
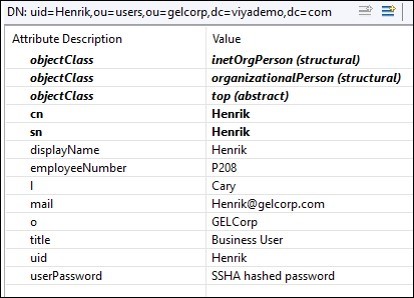
The attribute value pairs are the details of the entry.
The objectclass attribute is worth a special mention. Every entry has at least one objectclass attribute and often more than one. The objectclass is used to provide the rules for the object including required and allowed attributes. For example, the inetorgperson object class specifies attributes about people who are part of an organization, including items such as uid, name, employeenumber etc.
LDAP Tree
Let’s now look at the organization of the tree. DC is the “domain component.” You will often see examples of LDAP structures that use DNS names for the domain component, such as: dc=sas,dc=com. This is not required, but since DNS itself often implies organizational boundaries, it usually makes sense to use the existing naming structure. In this example the domain component is “dc=geldemo,dc=com”. The next level down is the organizational unit (ou). An organizational unit is a grouping or collection of entries. Organizational units can contain additional organizational units.
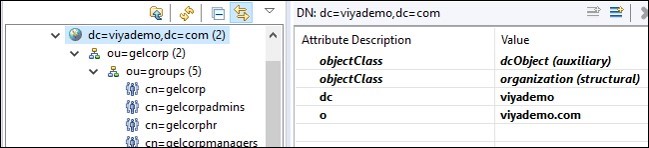
But how do we find the objects we want in the directory tree? Every entry in a directory has a unique identifier, called the Distinguished Name (DN). The distinguished name is the full path to the object in the directory tree. For example, the distinguished name of Henrik is uid=Henrik,ou=users, ou=gelcorp,dc=viyademo,dc=com. The distinguished name is the path to the object from lowest to highest (yes it seems backward to me to).

LDAP Queries and Filters
Like any other database LDAP can be queried and it has its own particular syntax for defining queries. LDAP queries are boolean expressions in the format
attribute operator value
uid = sasgnn
Attribute can be any valid LDAP attribute (e.g name, uid, city etc.) and value is the value that you wish to search for. The usual operators are available, including:
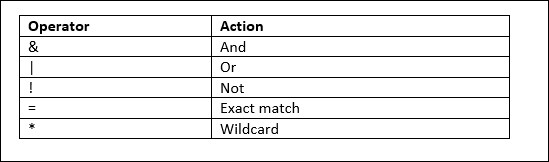
Using LDAP filters, you can link two or more Boolean expressions together using the “filter choices” and/or. Unusually, the LDAP “filter choices” are always placed in front of the expressions. The search criteria must be put in parentheses and then the whole term has to be bracketed one more time. Here are some examples of LDAP queries that may make the syntax easier to follow:
- (sn=Jones): return all entries with a surname equal to Jones.
- (objectclass=inetorgperson) return entries that use the inegorgperson object class.
- (mail=*): return all entries that have the mail attribute.
- (&(objectclass=inetorgperson)(o=Orion)): return all entries that use the inetorgperson object class and that have the organization attribute equal to Orion (people in the Orion organization).
- (&(objectclass=GroupofNames)(|(o=Orion)(o=Executive))) return all entries that use the groupofNames object class and that have the organization attribute equal to Orion OR the organization attribute equal to Executive (groups in the Orion or Executive organizations).
Why do I need to know this?
How will you apply this LDAP knowledge in SAS Viya? To enable SAS Viya to access your identity provider, you must update the SAS Identities service configuration. As an administrator, the most common items to change are:
- BaseDN the entry in the tree from which the LDAP server starts it search.
- ObjectFilter the filter used to identity and limit the users and groups returned.
There is a separate BaseDN and ObjectFilter for users and for groups.
To return users and groups to SASVIYA from our example LDAP server we would set:
sas.identities.providers.ldap.group.BasedN=ou=gelcorp,ou=groups,dc=viyademo,dc=com sas.identities.providers.ldap.users.BasedN= ou=gelcorp,ou=users,dc=viyademo,dc=com
This would tell SASVIYA to begin its search for users and groups at those locations in the tree.
The object filter will then determine what entries are returned for users and groups from a search of the LDAP tree starting at the BaseDN. For example:
sas.identities.providers.ldap.group.objectFilter: (&(objectClass=GroupOfNames)(o=GELCorp LTD)) sas.identities.providers.ldap.users.objectFilter: (&(objectClass=inetOrgPerson)(o=GELCorp LTD))
There are a lot of LDAP clients available that will allow you to connect to an LDAP server and view, query, edit and update LDAP trees and their entries. In addition, the ldif file format is a text file format that includes data and commands that provide a simple way to communicate with a directory so as to read, write, rename, and delete entries.
This has been a high-level overview of LDAP. Here are some additional sources of information that may help.

4 Comments
Thats's very useful.
I would like to ask you if there is a way to gather all users from different groups in the ObjectFilter attribute, I mean, I have 5 different groups on LDAP at he same level I would like to know if this is supported or how can I can concatenate many groups in order
Hi Carlos, a bit late perhaps: a normal ldap query cannot accomplish this, you will not be able to load all users to the application.
What you likely need is to search your base using the global catalog, and apply a filter that will match your OU's (and thus your users).
Global catalog normally runs on port 3268 (plain) and 3268 (tls)
For more information see:
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-2000-server/cc978012(v=technet.10)?redirectedfrom=MSDN
Very useful Gerry! Can you please give an example of specifying an LDAP filters for allowing only 3 specific users?
Thank you in advance!
Glad you found it useful. The following filter uses the or (|) operator to restrict the users returned to only the three uid's.
(|(uid=Sebastian)(uid=Sheldon)(uid=sasadm))