SAS Viya 3.3 introduced a set of command-line interfaces that SAS Viya administrators will find extremely useful. The command-line interfaces(CLI) will allow administrators to perform numerous administrative tasks in batch as an alternative to using the SAS Environment Manager interface. In addition, calls to the CLI’s can be chained together in scripts to automate more complex administration tasks. In the post I will introduce the administration CLI’s and look at a few useful examples.
The sas-admin CLI is the main interface; it acts as a wrapper for the other CLI’s. The individual CLI’s operate as interfaces to functionality from with sas-admin. The CLI’s provide a simplified interface to the SAS Viya REST services. They abstract the functionality of the REST services allowing an administrator to enter commands on a command line and receive a response back from the system. If the CLI’s do not surface, all functionality you need, calls to the REST API can be made to fill in the gaps.
In SAS Viya 3.3 the available interfaces(plug-ins) within sas-admin are:
| Plugin | Purpose |
| audit | Gets SAS audit information. |
| authorization | Gets general authorization information, creates and manages rules and permissions on folders. |
| backup | Manages backups. |
| restore | Manages restore operations |
| cas | Manages CAS administration and authorization |
| configuration | Manages the operations of the configuration service |
| compute | Manages the operations of the compute service. |
| folders | Gets and manages SAS folders. |
| fonts | Manages VA fonts |
| devices | Manages mobile device blacklist and whitelist actions and information. |
| identities | Gets identity information, and manages custom groups and group membership |
| licenses | Manages SAS product license status and information |
| job | Manages the operations of the job flow scheduling service |
| reports | Manages SAS Visual Analytics 8.2 reports |
| tenant | Manages tenants in a multi-tenant deployment. |
| transfer | Promotes SAS content. |
The command-line interfaces are located on a SAS Viya machine (any machine in the commandline host group in your ansible inventory file) in the directory /opt/sas/viya/home/bin.
There are two preliminary steps required to use the command-line interface: you need to create a profile and authenticate.
To create a default profile (you can also create named profiles):
sas-admin profile set-endpoint “http://myserver.demo.myco.com”
sas-admin profile set-output text |
You can also simple enter the following and respond to the prompts.
sas-admin profile init |
The default profile will be stored in the user’s home directory in a file <homedir>/.sas/config.json
The output options range from text, which provides a simplified text output of the result, to full json which provides the full json output that is returned by the rest call which the CLI will submit. The full json output is useful if you’re piping the output from one command into a tool which is expecting json.
To authenticate:
sas-admin auth login –user sasadm –password ******** |
The authentication step creates a token in a file stored in the user’s home directory which is valid for, by default, 12 hours. The file location is <homedir>/.sas/credentials.json.
The syntax of a call to the sas-admin CLI is shown below. The CLI requires an interfaces(plugin) and a command.
The example shows a call to the identities interface. This command will list all the users who are members of the SAS Administrators custom group.
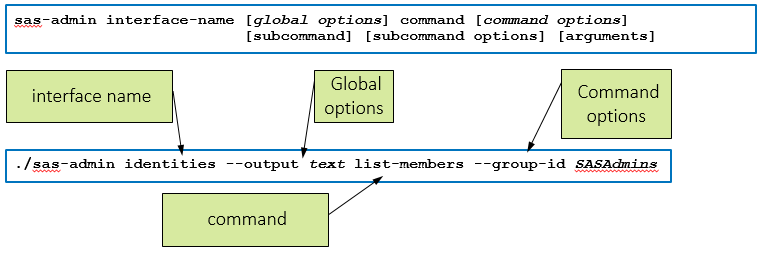
In this execution of sas-admin:
- the interface is identities.
- there is a global option –output set so that the result is returned in basic text.
- the command is list-members.
- the command option –group-id specifies the group whose members you wish to list.
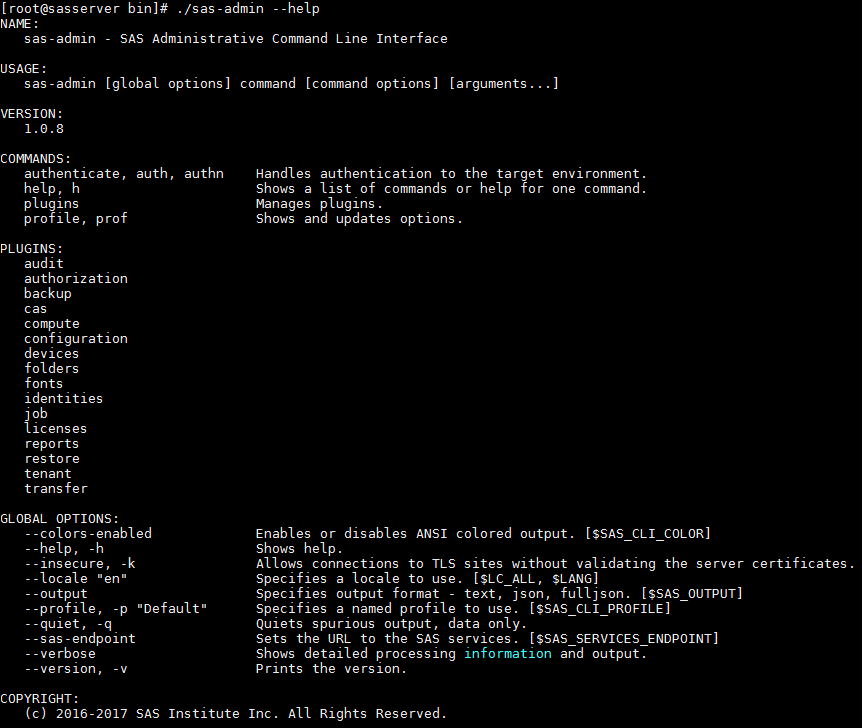
The built-in help of the CLI’s is a very useful feature.
./sas-admin --help |
This command provides help on the commands and interfaces(plugins) available, and the global options that may be used.
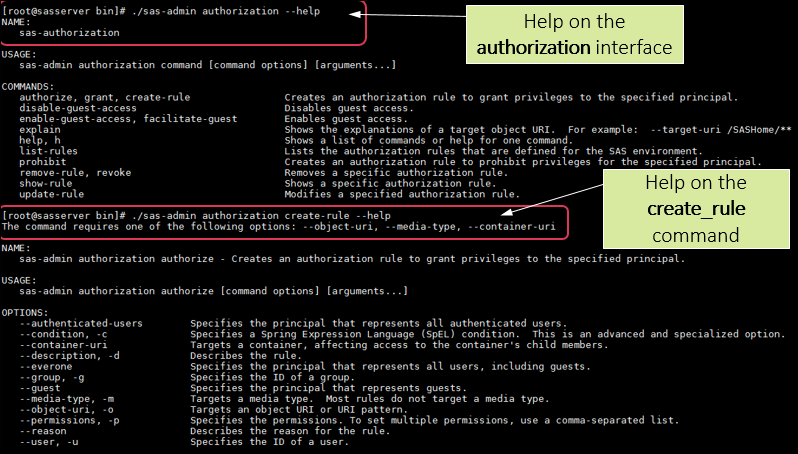
You can also display help on a specific interface by adding the interface name and then specifying –help.
./sas-admin authorization -–help |
Let’s look at an example of using the command-line interface to perform some common administrative tasks. In this example I will:
- create a new folder that is a sub-folder of an existing folder.
- create a rule to set authorization on a folder.
- create and secure a caslib.
Many of the folders commands require the ID of a folder as an argument. The id of the folder is displayed when you create the folder, when you list folders using the CLI and in SAS Environment Manager.
To return a folder id based on its path you can use a rest call to the /folders/folders endpoint. The json that is returned can be parsed to retrieve the id. The folders id can then be used in subsequent calls to the CLI. The rest api call below requests the id of the /gelcontent folder.
curl -X GET “http://myserver.demo.myco.com/folders/folders/@item?path=/gelcontent” -H “Authorization: bearer $TOKEN” | python -mjson.tool |
It returns the following json (partial)
{
“creationTimeStamp”: “2017-11-17T15:20:28.563Z”,
“modifiedTimeStamp”: “2017-11-20T23:03:19.939Z”,
“createdBy”: “sasadm”,
“modifiedBy”: “sasadm”,
“id”: “e928249c-7a5e-4556-8e2b-7be8b1950b88”,
“name”: “gelcontent”,
“type”: “folder”,
“memberCount”: 2,
“iconUri”: “/folders/static/icon”,
“links”: [
{
“method”: “GET”,
“rel”: “self”,
NOTE: the authentication token($TOKEN) in the rest call is read from the credentials.json file created when the user authenticated via sas-admin auth login. To see how this is done check out the script at the end of the blog.
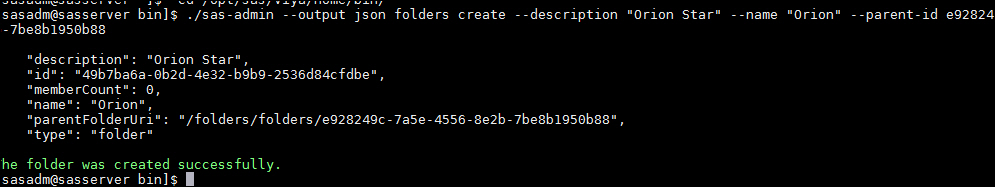
The next step is to create a folder that is a sub-folder of the /gelcontent folder. The id of the parent folder, and name of the new folder is passed to the create command of the folders interface.
./sas-admin –-output json folders create –-description “Orion Star” –-name “Orion” -–parent-id e928249c-7a5e-4556-8e2b-7be8b1950b88 |
Next using the folder id from the previous step set authorization on the folder. In this call to the authorization interface I will grant full control to the group gelcorpadmins on the new folder and its content.
./sas-admin authorization create-rule grant -–permissions read,create,update,delete,add,remove,secure -–group gelcorpadmins -–object-uri /folders/folders/49b7ba6a-0b2d-4e32-b9b9-2536d84cfdbe/** -–container-uri /folders/folders/49b7ba6a-0b2d-4e32-b9b9-2536d84cfdbe |
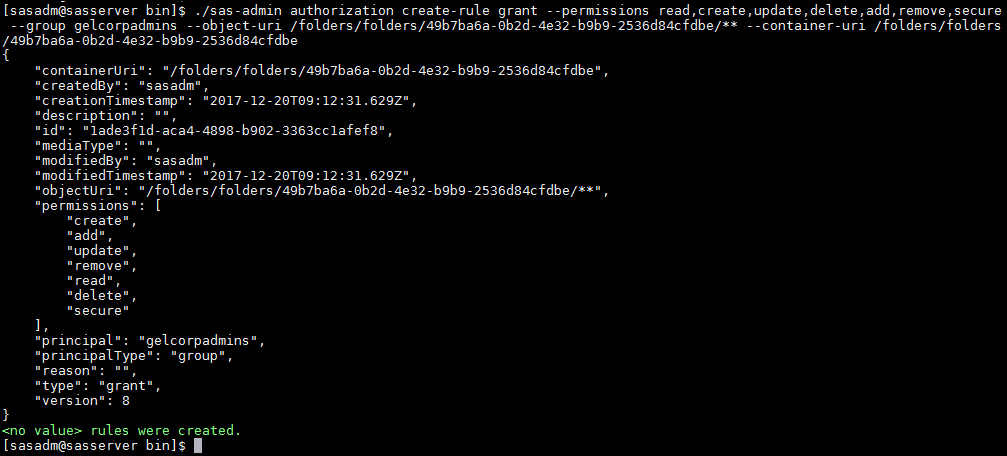
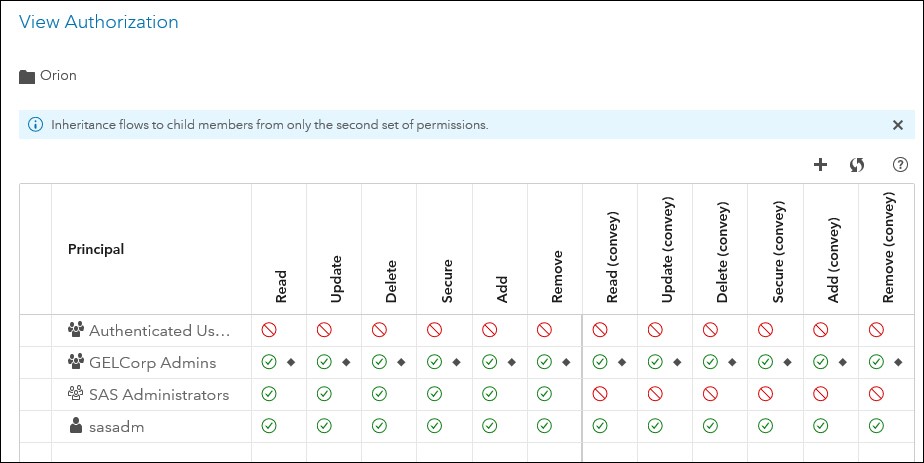
Now in Environment Manager, check that the folder has been created and check the authorization settings. The authorization setting on the folder shows that a new rule has been created and applied providing explicit full access to gelcorpadmins (whose user-friendly name is “GELCorp Admins”).
The next task we might perform is to add a caslib and set authorization on it. We can do that with the following calls to the cas interface.
./sas-admin cas caslibs create path -name ordata --path /tmp/orion --server cas-shared-default ./sas-admin cas caslibs add-control --server cas-shared-default --caslib ordata –-group gelcorpadmins –-grant ReadInfo ./sas-admin cas caslibs add-control --server cas-shared-default --caslib ordata --group gelcorpadmins –-grant Select ./sas-admin cas caslibs add-control --server cas-shared-default --caslib ordata --group gelcorpadmins --grant LimitedPromote |
#!/bin/bash clidir=/opt/sas/viya/home/bin/ endpoint=http://sasserver.demo.sas.com export TOKEN= export TOKEN=`grep access-token ~/.sas/credentials.json | cut -d’:’ -f2 | sed s/[{}\”,]//g ` #Get gelcontent folder id curl -X GET “$endpoint/folders/folders/@item?path=/gelcontent” -H “Authorization: bearer $TOKEN” | python -mjson.tool > /tmp/newfolder.txt id=$(grep ‘”id”:’ /tmp/newfolder.txt | cut -d’:’ -f2 | sed s/[{}\”,]//g) echo “The folder ID is” $id #Create orion Folder $clidir/sas-admin –output text folders create –name Orion –parent-id $id > /tmp/folderid.txt orionid=$(grep “Id ” /tmp/folderid.txt | tr -s ‘ ‘ | cut -f2 -d ” “) echo “The orion folderid is” $orionid # set permissions $clidir/sas-admin authorization create-rule grant –permissions read,create,update,delete,add,remove,secure –group gelcorpadmins –object-uri /folders/folders/$orionid/** –container-uri /folders/folders/$orionid $clidir/sas-admin authorization create-rule grant –permissions read –group gelcorp –object-uri /folders/folders/$orionid |
The SAS Viya command-line interfaces are a very valuable addition to the administrator’s toolbox. There is obviously much more which can be done with the CLI’s than we can cover in this article. For more information and details of the available interfaces please check out the SAS Viya 3.3 Administration Guide.

12 Comments
I would like to schedule a job with CLI on a jumpbox with crontab. The problem is that I have to provide my password for CLI so that the cronjob with script runs automatically. Is there an option that I can encode my password for CLI in the script?
Hi Karolina there is no option to encode a password for the CLI. One approach we take to pass the credentials securely is to use an authinfo file with the CLI. We have a tool in the pyviyatools loginviauthinfo.py that supports this approach. https://github.com/sassoftware/pyviyatools/blob/master/loginviauthinfo.md
Hi Gerry,
What is the difference between sas-viya and sas-admin when using the CLI ? thanks in advance for the details.
Seems like you never got an answer on this one.
sas-viya is for SAS Viya 4.
https://support.sas.com/downloads/package.htm?pid=2512
sas-admin is for SAS Viya 3.x
https://support.sas.com/downloads/package.htm?pid=2133
Hi Gerry,
Nice article ! thanks for sharing ..
I just wanted to know how to download the additional plugins for the sas-admin when the server does not have a internet connection ?
Can I download the plugins from a windows command line and move it into a linux machine ?
Is there a alternate way to get the same in a packaged form.
Hi Eileen, glad you found the article useful.
I would suggest installing the CLI and plugins on WSL on your Windows machine.
The plugins are installed in ~/.sas/admin-plugins. Also in this directory is a config.json file that references the location of the plugins.
You could then copy the directory contents to the Linux box in the Linux user's home directory, if the home directory is different you will need to edit the paths in config.json.
Make sure also that the Linux user has RWX permissions to the copied plugins. That should do it.
Is there a RESTFUL API to create, update and delete users, create, update and delete roles and groups and assign the groups/roles to users based?
Hi Sunil,
The identities plug-in is the documented interface to managing users and groups in VIYA, it can create custom groups and manage group membership. Viya users exist only in LDAP so creating/deleting/updating users would be done using LDAP tools.
How do you duplicate the SAS Adminstrators Rules into another custom group SAS Adminstrators Copy. I want customize the SAS Adminstrator Rule and want to remove User management capability for SAS Adminstrator
After you have created the account and is asked to authenticate, where do you get the user and password from?
After you create the profile. You can logon with the user account that you use to logon to SAS Viya.
Great article Gerry (as always)! Have a super day!