When we think of something “new”, we tend to picture something clean, shiny, or efficient. The new normal of fraud only checks one of those boxes, and unfortunately, that’s “efficient.” Today, scams and cyber attacks are persistent, and part of a larger ecosystem of phishing and hacking attacks by both organized criminal groups and nation-states.
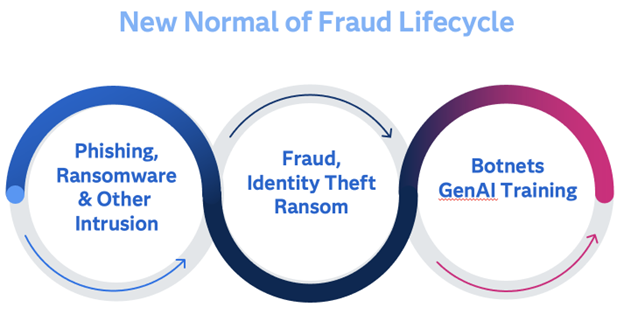
A good way to think of how this all fits together is the Fraud Life Cycle:
Every day, we hear about data breaches, organizations brought down by ransomware, and the results of human error from phishing attacks. United HealthGroup and their subsidiary Change Healthcare are now the subject of multiple federal probes after falling victim to a sophisticated ransomware attack from AlphV. What makes this situation unique? It brought pharmacies and medical providers to their knees. Americans couldn’t get their prescriptions filled for days or weeks, and medical providers aren’t receiving overdue payments, straining an already overtaxed system.
But beyond extracting a ransom of $22 million, what happens to the data from an attack like that, or so many others? It’s sold and resold throughout the dark web. Other criminal groups pick up that personal health care data, and all the other points about us floating around from other hacks, and steal our identities. Then the fraud penetrations begin. It could be the bank account takeover, the ever popular fake unemployment claim, false credit card charges, or come back to health care with fake claims to insurers. Add in the increasing romance scams, and fraud runs the gamut.
One reason for the dramatic expansion of the entire Fraud Lifecycle is the pervasiveness of the connected world. Almost any device with the word “smart” tied to it has some level of computer chips in it, and connects to wi-fi and the Internet. The second that happens, it becomes an exposure point. That includes light bulbs, door locks, cameras, and one I hadn’t thought about much until a recent study came out . . . toothbrushes. That’s right, the next risk could be lurking between your teeth. All of those devices can be hacked, and while some provide a bigger direct risk, like releasing video from the inside of your house, they can all become part of a botnet, which is simply a hacked network of devices used to generate the footprint to support the next phishing or ransomware attack.
The latest layer on top of this entire cycle is how Generative AI plays in. It not only allows development of fake information with a higher degree of realism to be generated at scale quickly, it can also train on your own stolen data to more easily replicate fake submissions. This can play out not only on text, but also voice and image data as well.
All is not lost, however. But it will take more vigilance on the part of individuals and organizations to prevent ever more sophisticated phishing, smishing (text) or “vishing” (calls/voice) attacks from working. Locking down connected devices, awareness of data leaks and the proactive use of AI and data can help to stem the tide. In a recent study from the Association of Certified Fraud Examiners (ACFE) and SAS, 80% of fraud-fighters are expecting to deploy Generative AI by 2025, a very positive development.
Check out the 2024 Anti-Fraud Technology Benchmarking Report from SAS and ACFEWhile individuals should remain wary of the various fraud landmines in their personal lives, agencies and authorities need smart solutions with advanced capabilities to keep up with this dangerous new environment. Solutions like SAS Payment Integrity for Social Benefits and SAS Tax Compliance approach detection and prevention with cutting edge hybrid approaches to data and AI to help address the constant barrage of organized attacks.