 In this article, I want to give you an overview of the authentication options available with SAS Viya 3.3. SAS Viya 3.3, released in the second week of December 2017, and the second release with the new microservices architecture, presents more options for authentication than the previous releases. In future posts, we will delve in to more detail for a select option.
In this article, I want to give you an overview of the authentication options available with SAS Viya 3.3. SAS Viya 3.3, released in the second week of December 2017, and the second release with the new microservices architecture, presents more options for authentication than the previous releases. In future posts, we will delve in to more detail for a select option.
Types of Deployment
Before we look at the options for authentication we need to define some terms to help us describe the type of environment. The first of these is the type of deployment. With SAS Viya 3.3 we can have two different types of deployment:
- Full Deployment
- Programming Only
As the name suggests, the full deployment is a deployment of all the different components that make up the ordered SAS Viya 3.3 product or solution. This includes the SAS Viya runtime engine, CAS (Cloud Analytic Services), the microservices, stateful services, and foundation components used by SAS® Studio.
The programming only deployment more closely resembles the deployment we saw in an earlier release; so, this includes CAS and all the parts for SAS Studio to function. A programming only deployment does not include the microservices and stateful services. The only interaction with CAS is via SAS Studio and the code end-users run within this.
Types of Interfaces
Following on from the type of deployment, we can classify the end-user interfaces used to access SAS Viya 3.3. The interface could be a visual interface or a programming interface. For a visual interface, we group all the SAS Viya 3.3 web applications, excluding SAS Studio. For a programming interface we mean SAS Studio. Equally within programming interface, when we say a programming interface accesses CAS we could also mean the Python, Lua, R or Java interfaces.
Similarly, as of the fifth maintenance release of SAS 9.4 we can interact directly with CAS. Previously, this interaction was based around the use of SAS/CONNECT® and remote submitting code to the SAS Viya programming interface. With SAS 9.4 M5, we can now directly connect to CAS from the SAS foundation. So, a third type of interface for us to consider is the SAS 9.4 M5 client.
Visual Interfaces Authentication
As we know with SAS Viya 3.3, the way the end-user authenticates to the visual interfaces is via the SAS® Logon Manager. The SAS Logon Manager is accessed via the HTTP Proxy. The following picture summarizes the options for authenticated to the SAS Logon Manager in SAS Viya 3.3.
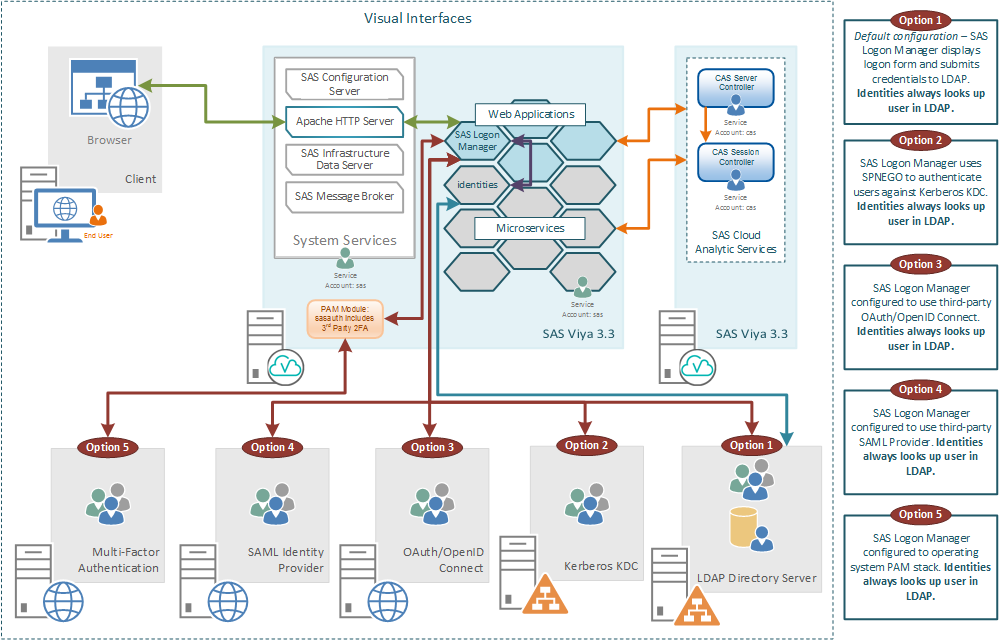
The first thing to point out and something to always remember is the following:
The identities microservice always must connect to an LDAP provider to obtain user and group information.
This LDAP provider could be Microsoft Active Directory or any other LDAP provider such as OpenLDAP.
So, what are our options for authenticating the users accessing SAS Logon Manager? We have five options with the SAS Viya 3.3:
1. LDAP Provider (the default option)
2. Kerberos or Integrated Windows Authentication
3. OAuth/OpenID Connect
4. SAML
5. Multi-factor Authentication (New with SAS Viya 3.3)
Option 1 is the default authentication mechanism enabled out-of-the-box for SAS Viya 3.3 is the LDAP Provider. The same connection details used by the identities microservice are used by SAS Logon Manager to authenticate the credentials the end-user enters in the logon form. From a security perspective, we need to be concerned about what network connections these end-user credentials will be sent over. First, we have the network connection between the browser and the HTTP proxy, which is secured by default with HTTPS in SAS Viya 3.3. Then we have the network connection between SAS Logon and the LDAP Provider, here we can support LDAPS to encapsulate the LDAP connection in standard TLS encryption.
Option 2, as shown in the diagram, is to configure SAS Logon Manager for Kerberos authentication. This provides the end-user with Single Sign-On from their desktop where the browser is running. This is sometimes referred to as Integrated Windows Authentication (IWA). This will enable the end-user to access the SAS Viya 3.3 visual interfaces without being prompted to enter any credentials. However, it is important to remember that the identities microservice will still be connecting to the LDAP provider. The Kerberos authentication option completely replaces the option to use the default LDAP provider for the SAS Logon Manager. Introduced with SAS Viya 3.3 is the option to delegate the credentials from SAS Logon Manager through to CAS; more on this option below.
Option 3 enables the SAS Logon Manager to be integrated with an alternative OAuth/OpenID Connect provider. This provider could be something internal to the customer’s wider environment or could be external to the customer, such as Google Auth of Facebook. When the OAuth/OpenID Connect option is configured this does not completely replace the default LDAP provider. Instead when the end-user accesses the SAS Logon Manager they are presented with a link to authenticate using OAuth/OpenID Connect and the standard login form using the LDAP provider. The end-user can then select which to use. This option can provide single sign-on from the OAuth/OpenID Connect provider;for example, sign into your Google account and access the SAS Viya 3.3 visual interfaces without further prompting for credentials. Custom code can be added to the SAS Logon Manager login form that automatically links to the external OAuth/OpenID Connect provider. This makes the single sign-on more seamless, since there is no need to select the link.
Option 4 supports configuring the SAS Logon Manager to be integrated with an external SAML Identity Provider. This SAML Identity Provider could be internal or external to the customer’s wider environment. If it is internal it could be something like Oracle Access Manager or Active Directory Federation Services, whilst if its external it could be something like salesforce.com. Again, like option 3, the use of SAML does not completely replace the default LDAP provider. End-users accessing the SAS Logon Manager will be able to choose SAML authentication or the default LDAP provider. Also, this option provides single sign-on with the third-party SAML provider. Custom code can be added to the SAS Logon Manager login form that automatically links to the external SAML provider, making the single sign-on more seamless, since there is no need to select the link.
Option 5 supports the use of Multi-factor authentication with SAS Logon Manager. This is a new option (with SAS Viya 3.3) and requires the configuration of a third-party Pluggable Authentication Module (PAM). This PAM module is the part of the system that integrates with the multi-factor authentication provider such as Symantec’s VIP. The PAM module authenticates the end-user by causing the third-party to push an out-of-band validation request to the end-user. Normally, this would be a push message to a smart phone application, approving the request forms the additional factor in the authentication of the end-user. When an end-user enters their username and password in the SAS Logon Manager form they are checked against the PAM provider. This means this option replaces the LDAP provider, just as with Kerberos.
For all five options listed above, the connection to CAS is performed using internal OAuth tokens generated by the SAS Logon Manager. In most cases the actual session started by the CAS Controller will now run on the operating system as the same user who launched the CAS operating system service. This account defaults to the name cas.
The exception to this is Option 2: Kerberos with delegation. In this case while an OAuth token is generated and initially used to connect to CAS a second authentication takes place with the delegated Kerberos credentials. This means that the CAS session is started as the end-user and not the user who launched the CAS operating system service.
Programming Interfaces Authentication
Now we’ve looked at the visual interfaces for SAS Viya 3.3, what about the programming interfaces or SAS Studio? Unlike SAS 9.4, SAS Studio with SAS Viya 3.3 is not integrated with the SAS Logon Manager. The following diagram illustrates the case with SAS Studio.
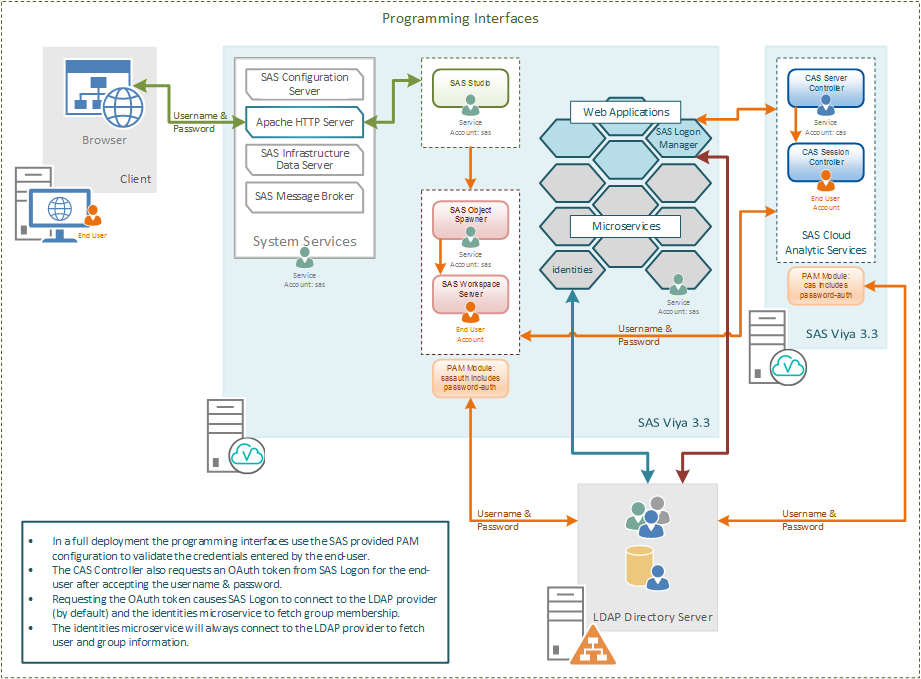
SAS Studio in the full deployment is integrated with the HTTP Proxy, so with SAS Viya 3.3 end-users do not directly connect to the SAS Studio web application. However, the username and password entered into SAS Studio are not passed to the SAS Logon Manager to authenticate. Instead the SAS® Object Spawner uses the PAM configuration on the host to validate the username and password. This could be a local account on the host or, depending on the PAM configuration, an account in an LDAP Provider. This authentication is sufficient to start the SAS® Workspace Server where the code entered in SAS Studio will be run.
When the SAS Workspace Server connects to CAS it uses the username and password that were used to start the SAS Workspace Server. The CAS Controller uses its own PAM configuration to validate the end-user’s credentials and launch the session process running as the end-user.
Since CAS is integrated into the visual components, and the username and password are passed from the SAS Workspace Server, the CAS Controller uses them to obtain an internal OAuth token from the SAS Logon Manager. This means that the username and password must be valid in the provider configured for the SAS Logon Manager otherwise CAS will not be able to obtain an OAuth token and the session launch will fail.
Therefore, it makes sense in such a deployment for all the three components:
1. PAM for SAS Studio (sasauth*)
2. PAM for CAS (cas)
3. SAS Logon Manager
to all use the same LDAP Provider. If these three components are not sending the username and password entered in SAS Studio to the same place we are likely to see errors when trying to connect.
Programming Only Deployment
For a programming only deployment, we have SAS Studio and CAS but we don’t have any microservices or stateful services. So here all authentication is via the PAM configuration for SAS Studio and CAS. Since CAS knows there are no microservices, it does not attempt to obtain an internal OAuth token from the SAS Logon Manager, the same type of setup we had for SAS Viya 3.1.
SAS 9.4 Maintenance 5 Integration
There are three main ways in which SAS 9.4 Maintenance 5 can integrate with CAS. First, if the SAS 9.4 M5 session has access to a Kerberos credential for the end-user, then Kerberos can be used for the authentication. For example, if Kerberos is used by the end-user to access the SAS 9.4 M5 client, such as a web application or SAS Enterprise Guide, the authentication can be delegated all the way through to CAS. Kerberos will then be used to authenticate to SAS Viya Logon Manager and obtain an OAuth token.
Second, if the SAS 9.4 M5 session has access to the end-user’s username and password; either from the cached credentials used to launch the session, an authinfo file, or from SAS 9.4 Metadata, then these credentials can be used to authenticate to CAS. The username and password will be used to launch the CAS and obtain an OAuth token from SAS Viya Logon Manager. This will be like the programming approach we detailed above.
Finally, for SAS 9.4 Maintenance 5 sessions which are not running as the end-user, we also have a solution. These sessions could be SAS® Stored Process or Pooled Workspace Server sessions, or even a SAS token launched workspace server. For these sessions, we can leverage the SAS® 9.4 Metadata Server to generate a one-time-password. This is the same way in which the SAS Stored Process itself is accessed. To be able to leverage the One-Time-Password with CAS, additional configuration is required in SAS Viya Logon Manager. SAS Viya Logon Manager must be configured with the details of the location of the URL for the SAS® 9.4 Web Infrastructure Platform. The services in the SAS 9.4 Web Infrastructure Platform will be used to validate the One-Time-Password. All this means that CAS can be accessed from a SAS 9.4 Metadata aware connection where end-user Operating System credentials are not available.
Conclusion
I hope that this overview has provided some context to the different types of authentication happening within and to a SAS Viya 3.3 deployment. Understanding the types of authentication available will be important for helping customers to select the best options for them. In future blog posts, we’ll look at the different new options in more detail.

8 Comments
Hi currently we are using SAS Viya 3.4 and we need to assign dynamically roles to users according to the roles and groups getting from the LDAP and then how to integrate these users with SAS DataSets in CAS lib in Visual Analytics to give permission to reports based on there roles and group.
Currently, we are using row-level grant in Visual Analytics and through code as followed below: -
cas mysession;
proc cas;
accessControl.updSomeAcsTable /
acs={
{caslib="row_lvl",
table="row_level.sas7bdat",
identity="XYZ",
identityType="User",
permType="Grant",
permission="Select",
filter="upcase(ABC)=upcase('SUB::SAS.Userid')"}};
quit;
cas mysession terminate;
Is there a way where we could integrate LDAP roles along with row-level filters in SAS Visual Analytics.
Hello Sagar,
This post is on authentication rather than authorization. I'd encourage you to look at the post "Examples of row-level security in SAS Viya" by my colleague David Stern. Where he walks through applying row-level security using LDAP groups. Also I would recommend reviewing the documentation for Identity-Based Substitution and the example to set a dynamic row-level filter.
Stuart
Dear Team,
We want to enable Web SSO for SAS Viya environment for which google is the identity provider. We have configured Google LDAP as identity provider and client is able to login using google email ID successfully. Could you please provide for reference on how to implement the same.
Hello Girish,
I assume that when you say "web SSO" you mean that once signed into your Google account you are able to use Single Sign-On to access SAS Viya. For this you will want to look at configuring OpenID Connect. This is covered in the documentation here: https://go.documentation.sas.com/?cdcId=calcdc&cdcVersion=3.4&docsetId=calauthmdl&docsetTarget=n1pkgyrtk8bp4zn1d0v1ln4869og.htm&locale=en#p1ubaum4cjrxu1n13tlf8ty60d4d.
Also I have some SAS Communities content on OpenID Connect here: https://communities.sas.com/t5/SAS-Communities-Library/SAS-Viya-3-2-External-OAuth-for-SAS-Logon/ta-p/372098 and here: https://communities.sas.com/t5/SAS-Communities-Library/SAS-Viya-3-4-Simplified-SAML-or-OpenID-Connect-Integration/ta-p/575811.
Stuart
Hello Sharanjeet,
This SAS Global Forum paper should help explain how to do this: https://support.sas.com/resources/papers/proceedings15/SAS1385-2015.pdf
Although the paper gives examples using Microsoft ADFS as the SAML identity provider, the configuration should be similar for OKTA.
Mike
I want to enable multi factor authentication with SAS VA 9.4 to use SAML authenticate with OKTA. Can you provide any guidance?
We are in process of implementing SAS Viya and have a need for configuring WebSOO for SAS VA. We have informed that WebSSO integration is not possible because of Identities services. Can you please share your thoughts on this.
Hello Ved,
Thank you for taking the time to comment. Implementing Web Single Sign-On is a complex topic. However I would not say that the Identities service prevents configuring Web Single Sign-On. You need to remember that Identities needs to correctly identify the end-user in the configured LDAP provider. This means for something like Kerberos or Integrated Windows Authentication (IWA) it is pretty straight forward. Since you have Active Directory to enable Kerberos you can configure Identities against the same Active Directory and every works well. If you are instead looking at leveraging Federated Identity providers through SAML v2 or OAuth/OpenID Connect, you'll need to put more thought into the LDAP provider used by Identities. However, again there are options that make this setup easy - for example Active Directory Federation Services will provide both SAML v2 and LDAP so you'll get both.
I hope that this information has helped - please reach out through Technical Support if you have further detailed questions.
Thank you for your time.
Stuart