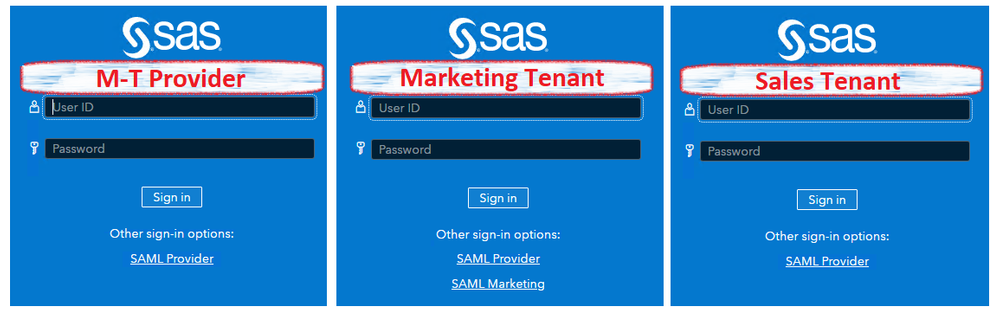
The SAS Viya LTS 2021.2 release supports application multi-tenancy. This 3-part series reviews how authentication can be configured.

The SAS Viya LTS 2021.2 release supports application multi-tenancy. This 3-part series reviews how authentication can be configured.
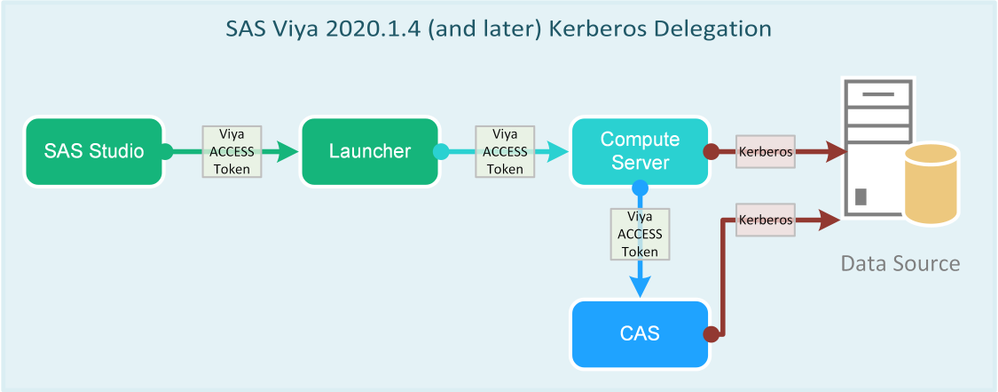
SAS Viya 2020.1.4 introduced support for Kerberos delegation. As a result, Kerberos delegation will be available with the Long Term Support release 2021.1. This series starts with an overview and continues into authentication processing in detail, Kerberos delegation configuration, and requirements for SAS/ACCESS to Hadoop. Part 1 - SAS Viya
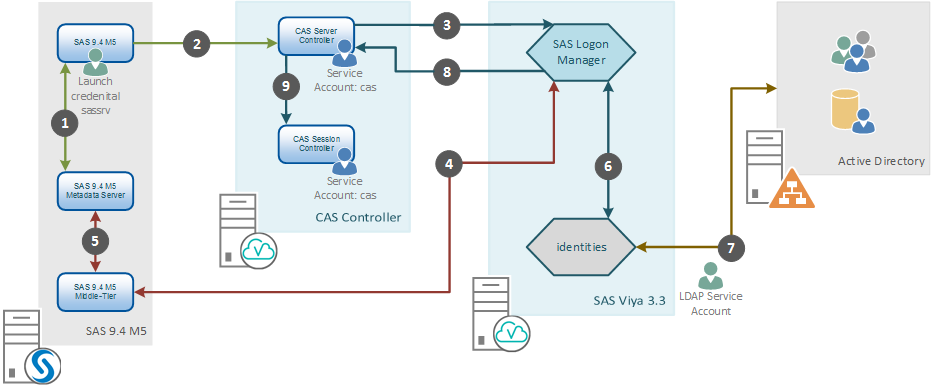
This post addresses connecting to SAS Viya using a One-Time-Password generated by SAS 9.4. We'll learn more about SAS Viya connecting with SAS 9.4 and talk about how this authentication flow operates and when we are likely to require it.